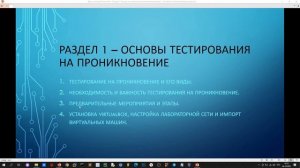
 5:04
5:04
2023-12-02 06:00
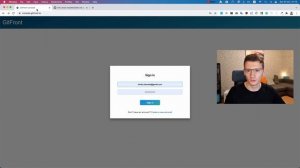
 2:41
2:41

 2:41
2:41
2023-12-04 14:56

 32:16
32:16

 32:16
32:16
2025-09-20 09:34
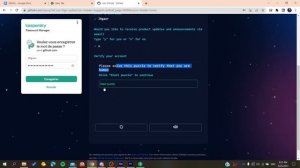
 2:31
2:31

 2:31
2:31
2023-12-04 14:49

 5:52
5:52

 5:52
5:52
2025-09-25 23:50

 0:36
0:36

 0:36
0:36
2025-09-26 18:00

 23:31
23:31

 23:31
23:31
2025-09-28 11:00

 8:30
8:30

 8:30
8:30
2025-09-12 15:00

 2:14
2:14

 2:14
2:14
2025-09-19 15:42

 34:56
34:56

 34:56
34:56
2025-09-12 16:44

 10:29
10:29

 10:29
10:29
2025-09-22 09:39

 1:11
1:11

 1:11
1:11
2023-08-15 18:54
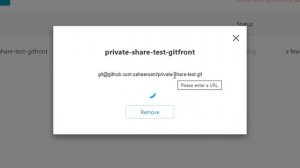
 7:12
7:12

 7:12
7:12
2023-09-13 15:51

 1:57:38
1:57:38

 1:57:38
1:57:38
2025-09-15 15:22

 27:58
27:58

 27:58
27:58
2025-09-20 10:00

 1:06:32
1:06:32

 1:06:32
1:06:32
2025-09-16 12:56

 7:40
7:40

 7:40
7:40
2025-09-25 17:00

 5:30
5:30
![Маракеш, Сергей Наговицын - До свидания, кореша (Премьера клипа 2025)]() 3:20
3:20
![Сирожиддин Шарипов - Хазонлар (Премьера клипа 2025)]() 3:09
3:09
![Вика Ветер - Еще поживем (Премьера клипа 2025)]() 4:31
4:31
![NYUSHA, ChinKong - Непогода (Премьера клипа 2025)]() 3:17
3:17
![ZAMA - Глаза цвета кофе (Премьера клипа 2025)]() 2:57
2:57
![Игорь Балан - Белая зима (Премьера 2025)]() 3:10
3:10
![10AGE, Роса ft. С. Есенин - Вот уж вечер (Премьера клипа 2025)]() 4:01
4:01
![Magas - Только ты (Премьера клипа 2025)]() 3:04
3:04
![Вусал Мирзаев - Слов не надо (Премьера клипа 2025)]() 2:19
2:19
![Антон Макарский - Не уходи (Премьера клипа 2025)]() 3:41
3:41
![Roza Zərgərli, Мурад Байкаев - Неизбежная любовь (Премьера клипа 2025)]() 2:34
2:34
![Марина Хлебникова, Russell Ray - Солнышко (Премьера клипа 2025)]() 4:42
4:42
![МАРАТ & АРНИ - Я ЖЕНИЛСЯ (Премьера клипа 2025)]() 4:16
4:16
![Tamo ft Djan Edmonte - Ну что красавица (Премьера клипа 2025)]() 3:10
3:10
![Соня Белькевич, Олег Семенов - Увы, мадам (Премьера 2025)]() 3:33
3:33
![Азамат Ражабов - Нигорим (Премьера клипа 2025)]() 3:52
3:52
![Рустам Нахушев - Письмо (Лезгинка) Премьера клипа 2025]() 3:27
3:27
![Гайрат Усмонов - Унутаман (Премьера клипа 2025)]() 5:17
5:17
![Жамхур Хайруллаев - Битта дона (Премьера клипа 2025)]() 2:49
2:49
![Соня Белькевич - Подогналась (Премьера клипа 2025)]() 3:13
3:13
![Рука, качающая колыбель | The Hand That Rocks the Cradle (2025)]() 1:44:57
1:44:57
![От заката до рассвета | From Dusk Till Dawn (1995) (Гоблин)]() 1:47:54
1:47:54
![Школьный автобус | The Lost Bus (2025)]() 2:09:55
2:09:55
![Кровавый четверг | Thursday (1998) (Гоблин)]() 1:27:51
1:27:51
![Большой куш / Спи#дили | Snatch (2000) (Гоблин)]() 1:42:50
1:42:50
![Супруги Роуз | The Roses (2025)]() 1:45:29
1:45:29
![Тот самый | Him (2025)]() 1:36:20
1:36:20
![Плохой Санта 2 | Bad Santa 2 (2016) (Гоблин)]() 1:34:55
1:34:55
![Крушащая машина | The Smashing Machine (2025)]() 2:03:12
2:03:12
![Только ты | All of You (2025)]() 1:38:22
1:38:22
![Чёрный телефон 2 | Black Phone 2 (2025)]() 1:53:55
1:53:55
![Протокол выхода | Exit Protocol (2025)]() 1:24:45
1:24:45
![Мужчина у меня в подвале | The Man in My Basement (2025)]() 1:54:48
1:54:48
![Дом из динамита | A House of Dynamite (2025)]() 1:55:08
1:55:08
![Гедда | Hedda (2025)]() 1:48:23
1:48:23
![Фантастическая четвёрка: Первые шаги | The Fantastic Four: First Steps (2025)]() 1:54:40
1:54:40
![Орудия | Weapons (2025)]() 2:08:34
2:08:34
![Французский любовник | French Lover (2025)]() 2:02:20
2:02:20
![Крысы: Ведьмачья история | The Rats: A Witcher Tale (2025)]() 1:23:01
1:23:01
![Плохой Cанта 2 | Bad Santa 2 (2016) (Гоблин)]() 1:28:32
1:28:32
![Сборники «Простоквашино»]() 1:05:35
1:05:35
![МегаМен: Полный заряд Сезон 1]() 10:42
10:42
![Пиратская школа]() 11:06
11:06
![Папа Супергерой Сезон 1]() 4:28
4:28
![Монсики]() 6:30
6:30
![Таинственные золотые города]() 23:04
23:04
![Ну, погоди! Каникулы]() 7:09
7:09
![Сборники «Зебра в клеточку»]() 45:30
45:30
![Люк - путешественник во времени]() 1:19:50
1:19:50
![Полли Покет Сезон 1]() 21:30
21:30
![Минифорс. Сила динозавров]() 12:51
12:51
![Пингвиненок Пороро]() 7:42
7:42
![Енотки]() 7:04
7:04
![Новогодние мультики – Союзмультфильм]() 7:04
7:04
![Отважные мишки]() 13:00
13:00
![Корги по имени Моко. Новый питомец]() 3:28
3:28
![Умка]() 7:11
7:11
![Шахерезада. Нерассказанные истории Сезон 1]() 23:53
23:53
![Мартышкины]() 7:09
7:09
![Команда Дино. Исследователи Сезон 1]() 13:10
13:10

 5:30
5:30Скачать Видео с Рутуба / RuTube
| 256x144 | ||
| 640x360 | ||
| 1280x720 | ||
| 1920x1080 |
 3:20
3:20
2025-11-11 00:28
 3:09
3:09
2025-11-09 16:47
 4:31
4:31
2025-11-11 12:26
 3:17
3:17
2025-11-07 13:37
 2:57
2:57
2025-11-13 11:03
 3:10
3:10
2025-11-07 14:48
 4:01
4:01
2025-11-11 17:26
 3:04
3:04
2025-11-05 00:49
 2:19
2:19
2025-11-07 14:25
 3:41
3:41
2025-11-05 11:55
 2:34
2:34
2025-11-05 11:45
 4:42
4:42
2025-11-06 13:16
 4:16
4:16
2025-11-06 13:11
 3:10
3:10
2025-11-07 13:57
 3:33
3:33
2025-11-07 15:10
 3:52
3:52
2025-11-07 14:08
 3:27
3:27
2025-11-12 14:36
 5:17
5:17
2025-11-06 13:07
 2:49
2:49
2025-11-06 13:20
 3:13
3:13
2025-11-14 11:41
0/0
 1:44:57
1:44:57
2025-10-29 16:30
 1:47:54
1:47:54
2025-09-23 22:53
 2:09:55
2:09:55
2025-10-05 00:32
 1:27:51
1:27:51
2025-09-23 22:52
 1:42:50
1:42:50
2025-09-23 22:53
 1:45:29
1:45:29
2025-10-23 18:26
 1:36:20
1:36:20
2025-10-09 20:02
 1:34:55
1:34:55
2025-09-23 22:53
 2:03:12
2:03:12
2025-11-07 20:11
 1:38:22
1:38:22
2025-10-01 12:16
 1:53:55
1:53:55
2025-11-05 19:47
 1:24:45
1:24:45
2025-11-13 23:26
 1:54:48
1:54:48
2025-10-01 15:17
 1:55:08
1:55:08
2025-10-29 16:30
 1:48:23
1:48:23
2025-11-05 19:47
 1:54:40
1:54:40
2025-09-24 11:35
 2:08:34
2:08:34
2025-09-24 22:05
 2:02:20
2:02:20
2025-10-01 12:06
 1:23:01
1:23:01
2025-11-05 19:47
 1:28:32
1:28:32
2025-10-07 09:27
0/0
 1:05:35
1:05:35
2025-10-31 17:03
2021-09-22 21:43
 11:06
11:06
2022-04-01 15:56
2021-09-22 21:52
 6:30
6:30
2022-03-29 19:16
 23:04
23:04
2025-01-09 17:26
 7:09
7:09
2025-08-19 17:20
 45:30
45:30
2025-09-17 18:49
 1:19:50
1:19:50
2024-12-17 16:00
2021-09-22 23:09
 12:51
12:51
2024-11-27 16:39
 7:42
7:42
2024-12-17 12:21
 7:04
7:04
2022-03-29 18:22
 7:04
7:04
2023-07-25 00:09
 13:00
13:00
2024-11-29 13:39
 3:28
3:28
2025-01-09 17:01
 7:11
7:11
2025-01-13 11:05
2021-09-22 23:25
 7:09
7:09
2025-04-01 16:06
2021-09-22 22:45
0/0

